In 2025, the topic of proxy servers remains relevant for technical and socio-political reasons. First, some countries have significant restrictions regarding access to independent media and social networks, and proxies can quickly bypass blocks without using a full VPN.
Second, proxies help maintain anonymity in networks by hiding IP addresses. Many websites can track users’ IP addresses, geolocation, and behavior, and with proxies, you can mask your digital footprint and hide your exact location.
What is a Proxy Server and How Does It Work?
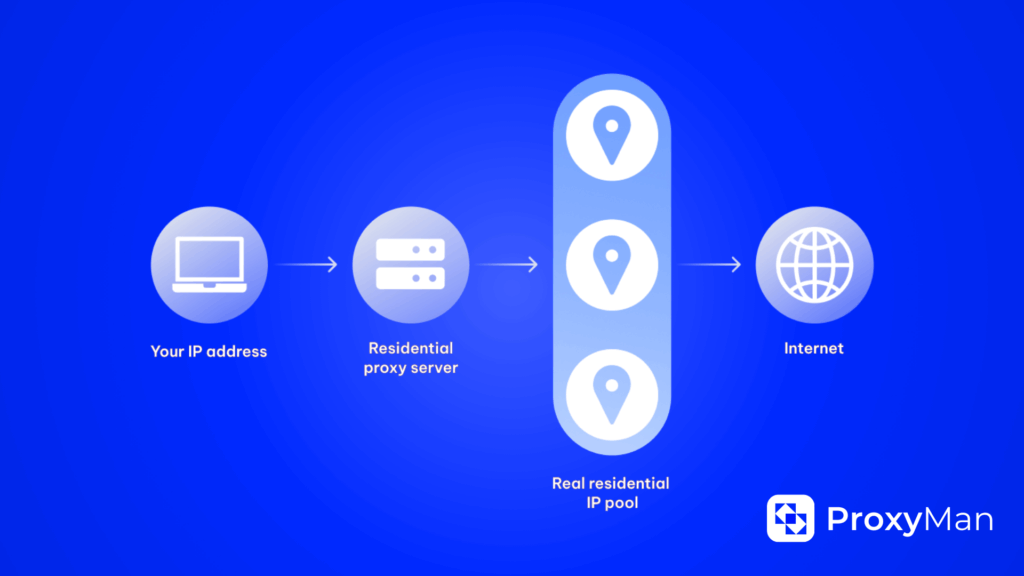
First, it’s necessary to understand what is a proxy server. This is a unique and modern technology that is often called an intermediary between the user and the target server. As a result, traffic is transmitted with the ability to hide the IP address and location of a specific user. Various data encryption protocols and anonymity methods are used for this purpose.
As soon as a user visits any website through a proxy server, their request automatically reaches the server, whose task is to forward the request to the website on behalf of that user. Thus, the website considers such user requests not as direct requests from computers, but as outgoing requests from proxy servers.
Main Types of Proxy Server and Their Differences
Having understood in more detail what is a proxy server and how does it work, it’s also necessary to study the main types and familiarize yourself with their distinctive features.
Today, the following popular types of proxy server are considered:
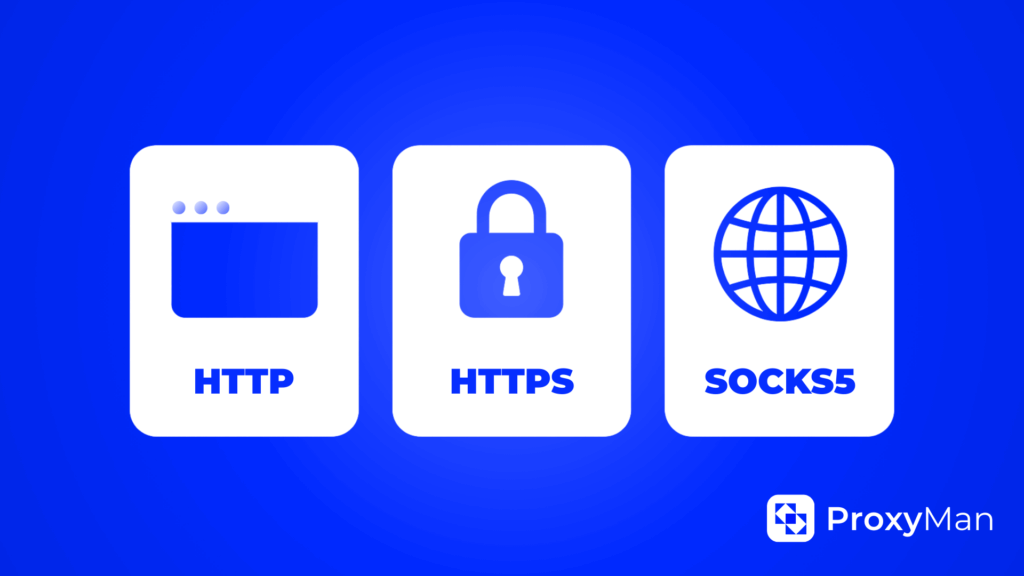
- HTTP – works exclusively with HTTP traffic, processing web requests (GET, POST), but doesn’t work with HTTPS and cannot guarantee special confidentiality.
- HTTPS – guarantees support for secure traffic, works using the HTTP CONNECT method, but is oriented exclusively toward web protocols (HTTP/S).
- SOCKS – this is a lower-level protocol that can redirect various data. It successfully supports authentication, web traffic (HTTP/HTTPS), games, torrents, email clients (SMTP, IMAP), but cannot encrypt traffic by itself.
As a result, the first two types will be sufficient for regular web surfing and local network control, and if protection, anonymity, and versatility are priorities, then SOCKS should be chosen.
What is a Common Function of a Proxy Server: Main Advantages
An increasing number of people choose proxy servers because they can provide reliable protection, control, and free access to the Internet.
Having determined what is a common function of a proxy server, it’s necessary to study the key advantages in more detail:
- Ability to bypass various types of blocks, gaining free access to websites from different regions.
- IP address change to maintain user anonymity, mask location, and avoid unwanted tracking by websites and providers.
- Maintaining anonymity along with necessary privacy on the Internet.
- Obtaining secure Internet access, as some proxy servers can filter malicious websites and ad trackers.
Additionally, proxy servers can cache data, thereby accelerating repeated user requests.
How to Use Working Proxy: Instructions for Using Proxy-Man
If you need a quality working proxy, you should use the capabilities of the Proxy-Man service. For this, it’s enough to go through a quick registration process in a few clicks to create a new account and gain access to all functionality.
After this, you need to perform the following steps:
- Go to the “Balance Top-up” section to make a payment to your account, choosing a convenient method.
- Go to the “New Proxy” page to decide on the appropriate type (Datacenter, Residential, or Mobile).
- Choose country, region, city, and internet service provider (ISP).
- Choose session type – maintaining the same IP addresses, setting up changes through time intervals.
- Choose the intended protocol – HTTP(S) or SOCKS5, deciding on a specific limit for proxy traffic. Everything is individual and depends on each user’s needs.
- After checking all previously selected parameters, click “Buy Now” to get access to your own proxy server.
- All generated proxy credentials need to be copied to paste them into applications, browsers, or other automation tools.
As a result, the Proxy-Man platform guarantees a high degree of security by maintaining anonymity. The user gets maximum protection from various network threats. Moreover, the platform works around the clock, so you can use any proxy server functions right now.
FAQ
Q: How to stay anonymous on the Internet while hiding your IP address?
A: For this, it’s recommended to use the unique capabilities of various proxy servers. They help not only hide IP addresses but also maintain confidentiality in the network and gain access to geographically restricted websites.
Q: Where can I get access to various types of proxy servers?
A: Various types of proxy servers are offered by the Proxy-Man platform, where you can rent proxies for any amount of time, using different quick payment methods.
Q: How to configure proxy servers on Proxy-Man?
A: For quick setup, you need to register, choosing the country and necessary list of settings for further work. If necessary, you can always contact Proxy-Man managers for free consultation.